Sam Broughton - Microsoft Security Consultant, Satisnet
Microsoft Cloud App Security (MCAS) is a Cloud Access Security Broker (CASB) that helps organisations to manage and protect their data stored in the cloud. MCAS provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats across all your cloud services and protect your data.
MCAS achieves this with the use of policies which are rules that are triggered once one or more conditions are met. Though MCAS comes with its out-of-the-box policies, it also provides you with the capability of customising your policies to allow you to monitor and secure threat vectors.
Access Policy
Access policies provide you with real-time monitoring and control with access to cloud apps for user, location, device. Access policies can be built for any device, including devices that are not Hybrid Azure AD joined, are not governed by Microsoft Intune, and do not obtain a valid client certificate.
Activity Policy
Activity policies allow you to implement a wide range of automated processes using the app provider’s API. These policies enable you to monitor specific movements, and actions carried out by your users or track unexpectedly high rates of one distinct type of activity.
Activity policies enable custom alerts to be sent and actions to be taken when suspicious user activity is detected. Example - force password change if the:
User tried to sign in and fails four times in one minute
Block specific files being sent externally
Disable a user account that is logged in from an unusual location
App Discovery Policy
The App discovery policy enables you to create alerts for new apps that are discovered in your organisation and will alert you when new apps are discovered within your environment. MCAS also searches all the logs in your Cloud Discovery for anomalies.
With this policy, you can set a threshold on how sensitive the policy should be by setting a criteria that the app must exceed daily to trigger the policy. These criteria include:
Daily traffic
Downloaded data
Number of transactions
Number of users
Uploaded data
Cloud Discovery Anomaly Detection Policy
A Cloud Discovery anomaly detection policy enables you to set up and configure continuous monitoring of unusual increases in cloud application usage. Increases in downloaded data, uploaded data, transactions, and users are considered for each cloud application. Each increase is compared to the regular usage pattern of the application as learned from past usage. The most extreme increases trigger security alerts.
File Policy
File policies can be set to provide compliance scans, DLP for sensitive content shared publicly, and many more use cases. Once enabled, the policy continuously examines your cloud environment and distinguishes files that match the content filters and then implements the automated actions upon detection. These policies detect and remediate any violations of stored or newly created files.
Examples of Custom File Policies in MCAS
Publicly shared files - Receive an alert about any file in your cloud that is publicly shared by selecting all files whose sharing level is public.
Publicly shared filename contains the organisation’s name - Receive an alert about any file that contains your organisation’s name and is publicly shared. Select files with a filename containing the name of your organisation and which are publicly shared
Sharing with external domains - Receive an alert about any file shared with accounts owned by specific external domains
Quarantine shared files not modified during the last period - Receive an alert about shared files that no one modified recently, to quarantine them or choose to turn on an automated action.
Sharing with unauthorised users - Receive an alert about files shared with an unauthorised group of users in your organisation
Sensitive file extension - Receive an alert about files with specific extensions that are potentially highly exposed. Select the specific extension (for example, crt for certificates) or filename and exclude those files with private sharing level
OAuth App Policy
An extension to the present investigation of OAuth apps connected to your cloud environment, you can establish permission policies so that you get automated notifications when an OAuth app matches your custom conditions. For example, you can be alerted when an app has been authorised to use OAuth by more than a certain amount of users.
OAuth app policies enable you to investigate which permissions each app requested, and which users authorised them for Office 365, G Suite, and Salesforce. You’re also able to mark these permissions as approved or banned. Marking them as banned will revoke permissions for each app for each user who authorised it.
Session Policy Microsoft Cloud App Security session policies allow real-time session-level monitoring, providing you granular visibility into the use of your cloud apps and the ability to take different actions depending on the policy you set for a user session. Rather than only allowing or blocking access entirely such as the Access policy. With session control, you can allow access to cloud apps while monitoring the session and blocking the users' activities during the session using the reverse proxy capabilities of Conditional Access App Control within MCAS.
For example, you can customise a session policy based on unmanaged devices, where you want to permit the user to access the cloud app but also restrict the download of sensitive files. Session policies allow you to create these user-session controls to enable you to:
Monitor all activities
Block all downloads
Block specific activities
Control files on download
Control files uploads of sensitive files
Block malware on upload
An example of a custom session control policy to block the download of confidential files from Office 365 for an unmanaged device can be created and configured by performing the following actions.
1. In the Create session policy page, give the custom policy a name and description. For example, Block downloads of Classified files from Office 365 for unmanaged devices.
2. Assign a Policy severity and Category.
3. For the Session control type, select Control file download (with inspection). This setting gives you the ability to monitor everything the specified users do within an Office 365 Exchange application session and provides control to block and protect downloads in real-time.

4. Under Activity source in the Activities matching all of the following section, select the filters:
· App: Select the app you want to control; in this case, it is Office 365
· Device: Select Tag, does not equal and then select one or more of the following options depending on the method used in your organisation for identifying managed devices:
- Intune compliant (Non-Compliant device)
- Hybrid Azure AD joined (Not on-prem or Azure AD domain joined)
- Valid client certificate (Invalid or expired client certificate)
· User: Select the users or group that the policy will apply to

5. Under Add file filter to the policy, select the parameter of the file detection method. Using Azure Information Protection (AIP) labelling capabilities, a customised label called ‘Confidential’ is chosen to trigger the policy if a file has this label attached.

6. Select Block and then choose whether also to notify the user by email or provide a custom block message once the user triggers the session policy.

7. Set the number of alerts you want to receive when the session policy is matched. You can set a limit of how many alerts you want to receive.
8. Select whether to receive the alerts as an email message, text message, or both and click Create
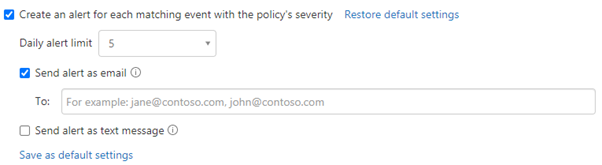
The session control custom policy that we have just created can be tested by carrying out the following actions:
1. From an unmanaged device, sign in to a Microsoft Office 365 app. The app will notify the user that their app session is being monitored through the MCAS proxy ‘cas.ms’ within the URL.

2. Then, try to download a file as the user that contains the word which matches the expression within the policy.
3. An alert message that was set under Customise block message

4. Within the MCAS portal, under Alerts, you should now see an alert detected by the session policy ‘Block downloads of classified files from Office 365 for unmanaged devices’ which was triggered by the user after attempting to download a confidential file from an unmanaged device. From here, an incident response investigation can be carried out.

Conclusion
MCAS provides a plethora of ways to detect cloud security threats within an organisation. Still, more importantly, it provides an easy, quick and efficient way of customising the detection methods to meet an organisation’s culture, requirements and goal to ensure cloud security from all angles of the business.
ABOUT SATISNET
Established in 2004, Satisnet Limited are a leading Security Integrator, Managed Security Services Provider (MSSP) and Cyber Training Innovator, with operations throughout the UK and EMEA. Boasting 60+ staff spread across three 24x7x365 UK-based, Security Operations Centres (SOCs) Satisnet are an industry-leader in the security/infrastructure space. A fledgeling Satisnet entered the cyber security space in 2002 focusing on a problem that few at the time recognised, namely vulnerability and patch management. Quickly establishing themselves as the EMEA leaders in this field, and partnering as Platinum Partners with key vendors in this space, Satisnet are excited to be partnering with another ‘Patch Powerhouse’ who are bringing a fresh approach to the space.
Extra References


Kommentarer